The 5 Best Cloud Security Companies and How to Decide
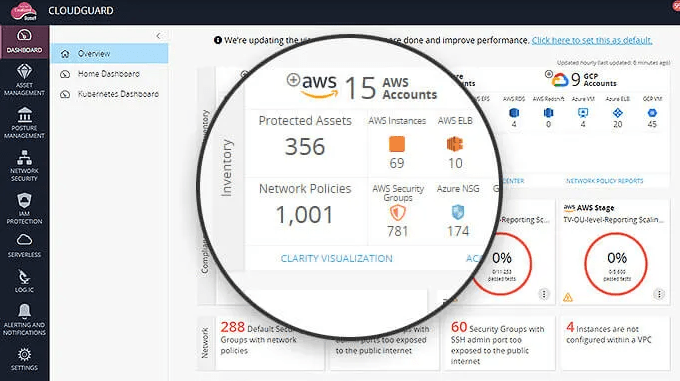
Cloud security companies help their clients visualize and control the ever-expanding perimeter that comes with moving operations and intellectual property outside the traditional moat and castle.
Patching together products from a mix of cloud security companies used to be the only solution for businesses with a complex, global IT infrastructure. To some degree, this is still the case: there is no omni-security solution, and even the best providers maintain a network of integrated partner and third party services.
That said, by choosing the right cloud security company, you can minimize the number of extra vendors involved, shrink your attack surface, and make your IT team’s life a lot more manageable.
Here’s a list of the top 5 cloud security companies that will help you keep every layer of every type of deployment impervious to attack. They offer multi-cloud ready solutions, built specifically for the way business is done tomorrow.
Palo Alto Networks
Palo Alto Networks is a well-respected leader in the cybersecurity community. Unit 42, the company’s global threat intelligence team, has played a role in responding to many of the most serious hacks of recent years. In 2018, they helped the U.S. Federal Bureau of Investigation bring down the Mirai Botnet.
Palo Alto Networks Prisma Cloud security platform provides an elegant combination of deep customizability and out-of-the-box functionality that gives IT teams a clear, real-time picture of security hygiene across the organization.
Prisma works for multi-cloud and hybrid environments, and comes with ready-made security solutions for public clouds like AWS, alibaba, Azure, Google Cloud, and IBM. It also helps companies using container and orchestration services like Docker, Kubernetes, or OpenShift gain increased visibility and control.
Once you connect your accounts, Prisma Cloud ingests and stores log data from across your IT ecosystem. From there, you can control everything with APIs or directly within the console, depending on your subscription. Prisma Cloud is available in three editions:
- Prisma Cloud Compute: Self-hosted, agent-based workload protection. Download the software and run it in private, public, hybrid, or air-gapped environments.
- Prisma Cloud Business: Hosted by Palo Alto Networks, delivered as SaaS. Use API to verify cloud deployments comply with security standards.
- Prisma Cloud Enterprise: Hosted by Palo Alto Networks, delivered as SaaS. Use API and agent-based approaches to secure cloud, hybrid, and multi-cloud environments. Includes advanced security tools.
Licensing for Prisma Cloud is a little unusual, but not overly complex. Each resource you protect with Prisma Cloud requires a certain number of credits. For example: hosts that run don’t run containers consume 1 credit, whereas hosts that do consume 7, regardless of the number of containers.
Like Check Point Software, Palo Alto Networks delivers a stunning range of enterprise-ready cloud security services. In addition to Prisma, Palo Alto offers the Strata and Cortex suites that provide uplevel defenses for legacy systems, and advanced security features to stop next generation threats.
Forcepoint
Forcepoint is a subsidiary of Raytheon, one of the largest defense manufacturers on the planet. They know how to keep devices secure whether they are on premise, in the cloud, in the actual clouds, or in orbit.
Their suite of security services gives your IT team a complete picture of the entire cloud ecosystem, and delivers enhanced response capabilities to solve the latest attacks. Forcepoint’s cloud security stack offers:
- Cloud Security Gateway
- Cloud Access Security Broker (CASB)
- Dynamic Edge Protection
- Email Security
- Web Filtering – URL Filtering
- Web Security
In addition to their dedicated cloud security products, Forcepoint offers vital data, network security solutions:
- Next Generation Firewall (NGFW)
- Data Loss Prevention (DLP)
- Insider Threat
- Behavioral Analytics
There are also cross-domain security products for companies with complex information sharing requirements and goals. Regardless of what you need, you can deploy, monitor, and configure all of these modular security services from a single dashboard.
The segmentation of Forcepoint products is very helpful to organizations that are looking to beef up security along certain attack vectors. They may require additional layers of protection and oversight where their cloud security provider’s responsibility ends.
Dynamic Edge Protection is a truly cloud native solution that functions as a complete Secure Access Service Edge (SASE). It’s cloud, data, network, and web security with advanced threat protection and zero trust network access. Wherever people are, they can safely access what they need without a hassle.
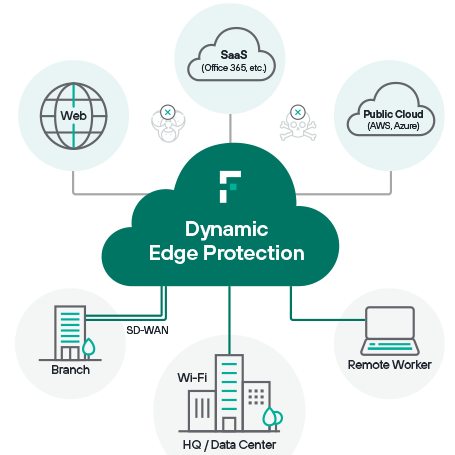
For financial services, healthcare, and other sectors that have to be extremely careful about data leakage, Forcepoint’s DLP solutions provide granular control, including the ability to audit and block transfers to USBs.
Some of the most notorious leaks in history have involved someone walking out the door with sensitive information in their pocket. With Forcepoint, you can stop these attacks before they start.
Check Point Software
Check Point Software began making firewalls nearly 30 years ago to combat novel cyberattacks on network systems. Since then, they’ve more than kept pace with hackers who exploit vulnerabilities in new technology, developing best-in-class endpoint, cloud, mobile, and IoT security solutions.
This is important because today’s most successful attacks are sophisticated, multi-vector attacks that target weakness across an organization’s IT ecosystem. Check Point Software is a leading cloud security company (they are Microsoft’s #1 security partner) because their feature-rich, scalable products streamline the process of protecting the entire perimeter.
For cloud native security, they offer a suite of CloudGuard products designed to keep data and intellectual property safe, regardless of how it is stored or used. Purpose-built CloudGuard products address:
- Branch office cloud security
- Container security
- Compliance and governance
- Email security
- Network security
- Privileged identity protection
- Productivity suite security
- Public or private cloud security
- SaaS security
- SD-WAN or uCPE security
- Serverless security
- Workload security
Cloudguard lets you oversee and protect assets across the entire developmental life cycle. With Security and Posture Management, you have total visibility into how users are accessing and updating cloud assets from remote locations. Control policies, roles, permissions, and enforce compliance automatically.

Check Point Software delivers as full a set of solutions as any cloud security company on the market.
Their suite of Sandblast products, for example, affords organizations best-in-class protection from zero day threats, whether no matter where they originate. You can automate the extraction, sandboxing, and sanitization of a wide range of file types.
This flips the script on attackers: the greater number of threats you face, the better your defenses become.
The benefit of an integrated suite of Check Point services is that companies can shift to a preventative cloud security stance without having to hire a ton of new people. Let your current IT team get ahead of fires with better tools that don’t slow down end user experience.
And, because they have such a deep product set and experience in the industry, Check Point can help you leverage your existing infrastructure and management tools to streamline deployment and further reduce total cost of ownership.
Akamai
Akamai Technologies is responsible for the world’s most highly distributed content delivery network (CDN), serving up to 30% of all internet traffic.
Each day, they detect and respond to millions of attacks. The security products they offer are continuously updated to reflect the latest intelligence across their vast network.
What’s nice about Akamai from an IT administrator perspective is that a relatively small number of tools can completely secure an organization. From its data centers to the ever-changing edge of its perimeter: applications, APIs, endpoints, users, and web applications. Their key cloud security offerings include:
- Enterprise Application Access
- Enterprise Threat Protector
- Kona Site Defender
- Page Integrity Manager
- Client Reputation
- Web Application Protector
- Prolexic Routed
- Zero Trust Security
Their products can be deployed rapidly, providing comprehensive cloud security that would require an impossible investment to establish in-house.
Enterprise Application Access and Enterprise Threat Protector function much the same way as the centralized consoles of other cloud security companies. It provides excellent protection from a range of attacks, incredible visibility into every aspect of your network, and simplifies all of the essential tasks necessary to maintain a strong security posture.
Akamai leverages their deep knowledge of CDN security to provide web application security that is virtually unrivaled. There’s a reason healthcare.gov uses Akamai.
The out-of-the-box functionality of Kona Site Defender is amazing. It uses the latest information from Akamai’s threat researchers and machine learning to surface real attacks quickly and limit the number of false positives.
With Kona Site Defender, all websites and APIs are protected, whether they are on premises or spread across multiple public clouds. It’s easy to get set up, but there are plenty of opportunities to finetune the tool to the specific needs of your organization.
Akamai’s products play well with others, enjoying longstanding partnerships with major cloud service providers. Along with the power and flexibility of their products, their reputation for quality customer support is another reason why many people choose Akamai over other cloud security companies.
Zscaler
Zscaler is one of many cloud security companies that claim to offer cloud native solutions, but one of the few to completely deliver on that promise. At its founding, the company decoupled from legacy networking ideas and designed a security service that reflected the realities of the modern workplace.
Instead of adding another appliance to your security stack, all traffic is routed through Zscaler cloud: mobile employees and remote offices can safely access internal and external resources via Zscaler rather than a private network.
Zscaler has experienced massive growth because their clients can gradually transition away from depreciating devices, shedding operational costs and IT drama. More clients and customers connecting to your cloud via Zscaler means less traffic on your WAN, which can translate to huge savings.
Zscaler is broken into two product suites:
- Zscaler Internet Access (ZIA)
- Zscaler Private Access (ZPA)
ZIA provides the secure connection your workers and customers need via a 100% cloud security stack that has next generation versions of the appliances you no longer need. DLP, firewalls, sandboxing, URL filtering—it’s all managed from a single console, and there is zero hardware to scale.
With ZPA, you get reliable, zero trust access to apps in the public cloud or data center. Apps connect outbound to authorized users only. Admins get deep control over segmentation at the application and user level.
Both ZIA and ZPA con in three editions: Professional, Business, and Transformation. Many of the individual services can be included as add-ons, allowing you to customize Zscaler to fit your exact needs.
How to choose the best cloud security company
Step 1: Map the perimeter
When you first start to look at various products from cloud security companies, it can be difficult to know where to start. There are an incredible amount of options and no end to the possible spend.
Making a sound decision starts with defining the scope of your cloud security needs. The truth is that your perimeter changes every time a device, user, app, or service is added. These days, even the smallest businesses have a fluid perimeter.
You want to pick products that can manage this reality according to your specific needs. Do you have tens of thousands of customers using your apps and sharing credit card information? Or is it a relatively small number of employees that need secure access to workloads from remote locations? Is it both?
Map your complete cloud ecosystem and budget in room for growth. How many devices, instances, containers, and so on will you need to protect?
Step 2: Model simplicity
Each cloud security company promises to keep your intellectual property and data safe, but how these services are delivered is quite different in each case.
What you are looking for is something that will simplify traffic flows, centralize management, and harden your entire ecosystem without adding extra burden on your employees and IT teams. Ideally, users will get faster access and admins will do more in less time.
Zscaler, among others on this list, offers purely cloud native solutions that you can connect to without having to reconfigure much of your existing architecture. If you are looking to add another appliance to your stack to address a specific issue, they won’t be much help.
Check Point Software, Forcepoint, Akamai, and Palo Alto Networks offer both hardware and SaaS solutions, which may make it easier for companies to leverage their existing infrastructures.
How well do the solutions in question work with your productivity suite and other cloud services? Zscaler, Check Point, and Palo Alto enjoy deep integration with Microsoft products, as well as AWS and Google Cloud.
Read up on what admins and executives are saying. Forcepoint works well to secure Microsoft 365, but on Mac people seem to run into issues.
Step 3: Protect the edge
Every provider on this list gives you a centralized platform with high visibility to manage the big name cybersecurity concerns. The task now is to match the specific capabilities of each service with the potential vulnerabilities you’ve identified by mapping your perimeter.
The biggest difference between cloud security companies can be found in the advanced features they offer, and how those features are split among service plans.
Forcepoint and Check Point provide modular services that can be tailored to fit any situation, whereas Zscaler, Palo Alto and Akamai offer broader service packages. The better you have defined your total cloud ecosystem, the better you can accurately forecast the services you need.
Step 4: Budget cost against cost of failure
You’ll have to get in touch with sales to get an accurate price for the service. Be candid about your expectations and concerns. The last thing you want is to be blindsided by a vulnerability you thought was covered.
Cloud security can get extremely expensive, especially for organizations with sensitive information and onerous compliance requirements. And even if the dollar amount is lower, cloud security represents a significant cost for smaller businesses trying to grow.
At the same time, accidental data leakage or an unblocked cyberattack can spell doom for a company. Ransomware attacks result in millions of dollars lost every year.
Finding a balance that keeps your organization safe without costs ballooning is difficult. If you find the right cloud security company to work with, it can make the process far easier.

