Enable JavaScript in Chrome with 5 Clicks
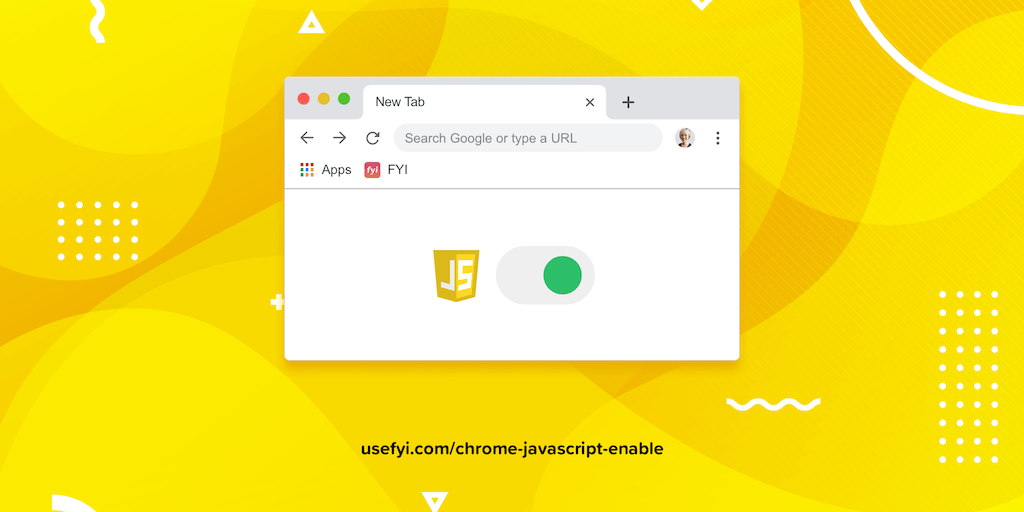
How do you turn JavaScript on and off in Chrome?
Here’s how to do it in just five clicks. And why you might want to turn it off completely.
Let’s get started.
1. Click Settings in the Chrome menu.
2. Select “Advanced” at the bottom of the Settings page.
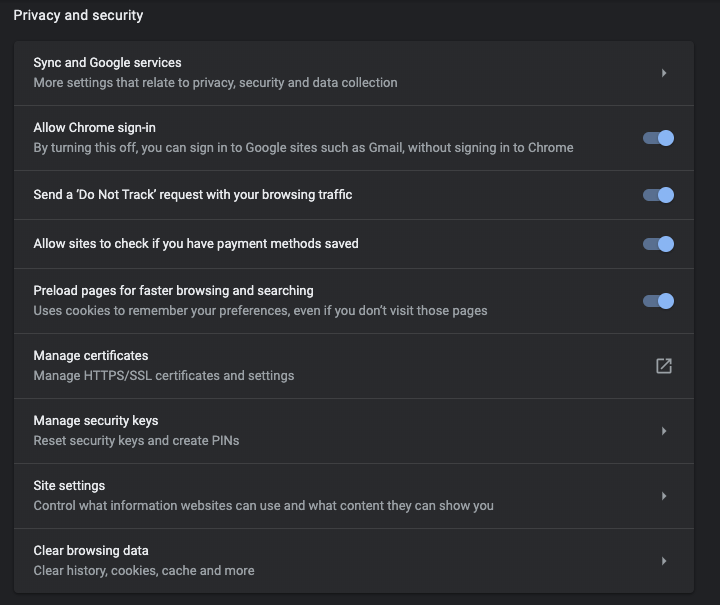
3. Under Privacy and security, scroll down to Site Settings.
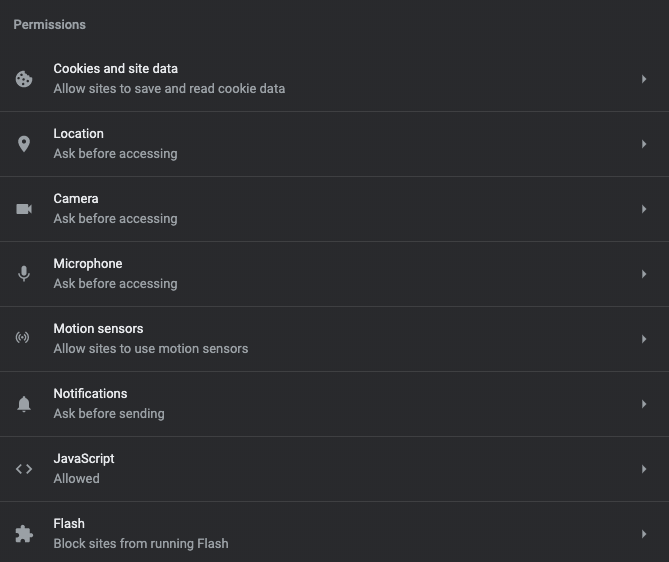
4. Click JavaScript.
5. Toggle to Allowed.
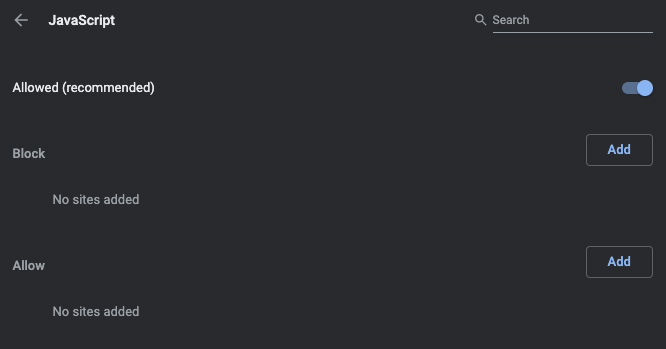
And you’re done!
Why should you enable JavaScript?
Most websites have JavaScript elements now.
Websites are built like this:
- HTML tells website elements where to be.
- CSS tells them how to look.
- JavaScript tells them what to do.
JavaScript basically handles interactive elements and things that move.
It’s the force behind everything from Google Docs to popups. The character counter on Twitter that lets you know if your tweet is too long? The credit card from your favorite online clothing store? Google Analytics? All JavaScript.
Facebook, YouTube, and other video sites are also heavily dependent on JavaScript.
The main reason to turn on JavaScript is so the internet works. Without JavaScript, the web is slightly faster, cleaner, and a lot less ads. But there’s a lot less stuff that you can do.
Is it safe to enable JavaScript?
JavaScript is so essential to the modern web that most browsers include a dedicated JavaScript engine just to run it. Most of the time, JavaScript is safe.
Many websites use the library of prewritten JavaScript called JQuery—it’s used by 73% of the 10 million most popular websites. And tools like Bootstrap also use third-party JS libraries. These are typically hosted by Google’s content delivery network and managed by teams that include security professionals. Many of these libraries do contain vulnerabilities but in practical terms, they’re usually safe to use.
JavaScript dates from a time when bandwidth was expensive and so was server space. Because JavaScript is executed on your computer, rather than on the servers of the websites you visit, it doesn’t strain server space or take up bandwidth. It’s an ideal choice for developers with limited resources.
But letting a website execute code on your computer is a security risk. JavaScript mitigates this by sandboxing. That means it doesn’t allow JavaScript access to the computer’s operating system or to web browser windows outside the one it loaded in. This sandboxing reduces the opportunities for malicious activity.
JavaScript is now ubiquitous. Since 95% of websites use JavaScript,it gets lots of attention from developers to make it more secure.
Overall, the threat is low enough that I wouldn’t turn off JavaScript for security unless you have a specific reason for doing so.
Why should you not enable JavaScript?
JavaScript is fairly safe to run in most browsers. But that’s not the same thing as “perfectly safe.” Because it’s a script from a website that’s executed on your computer, it can contain malware and exploits.
Most JavaScript that websites use is third-party library that’s open-source. The advantages of this approach are well-known. Nobody needs to reinvent the wheel and most JavaScript libraries are scrutinized by multiple skilled developers. Most of the time, this keeps things secure.
But it also means that when an organization uses these libraries, they’re trusting every developer who contributed. A single library could could have been built by hundreds of developers.
Deliberately malicious code in these libraries is super rare. But vulnerabilities do happen by accident often.
So how widespread is the issue?
About 80% of sites tested by Lighthouse had some vulnerable JavaScript, with an average of two libraries per page.
So most sites have a JavaScript vulnerability. Luckily, the risks are still low because:
- A bad actor has to target one of the sites you visit.
- You have to perform an action that puts you at risk (enter personal information, download something, etc).
- Most malware and viruses can be easily removed.
As long as you practice good browsing hygiene, the risks are low. Down’t download unknown files, don’t enter personal information in sites that you don’t trust, and avoid aggressive sites.
Popular JavaScript Attacks
During an attack, which methods are used most often?
Script injections
Script injections can be used to do anything from altering a website’s appearance to accessing user account data.
These attacks take advantage of the fact that your browser has the ability to interpret and turn on any script that’s embedded in HTML by default. So if attackers embed script tags like <SCRIPT>, <OBJECT>, <APPLET>, or <EMBED> into a website’s code, your browser’s JavaScript engine will run that script.
Cross-site scripting
Cross-site scripting (XSS) is a type of injection technique that allows the attacker to inject malicious code into a vulnerable web application to hijack the interactions users have with it.
It can be used to perform unauthorized activities and phishing attacks. It can also be used to capture keystrokes, stealing personal data and passwords in the process. Or to steal sensitive information directly.
Ads
One thing you’ll have notice with JavaScript turned on, there’s a lot more ads. If you’d like to have fewer ads without turning off JavaScript, there’s a number of popular Chrome Ad Blockers.
Ads are a popular attack route.
Suppose you click on an ad. Hidden inside the BMP (bitmap) file format that forms the image in the ad you’re looking it is compromised JavaScript that executes inside your browser. Since JavaScript is pretty safe, it doesn’t harm your computer directly. Instead, it redirects your browser to a fake website to harvest personal data or run scam competitions. BMP images like these are known as “Polyglot images” and this exploit of them is still relatively new.
Email attachments
JavaScript attachments are another common attack method. Far too many of us still open email attachments without checking them—let alone checking the file extension (.rtf, .docx, .csv, etc.) to see what type of file it is.
To make matters worse, Windows doesn’t show you these by default. And some criminals, wise to this, label files with double extensions, like this: suspicious.PDF.js.
The .js is the real extension, while the PDF is actually part of the file name. But when Windows suppresses the extension, the user sees suspicious.pdf. So criminals send emails with JavaScript attachments that insert malware that spams you, hijacks your browser, recruits your CPU to mine Bitcoin, or acts as a bridgehead for ransomware.
Lack of risk assessment
Finally, there’s the risk of undiscovered vulnerabilities arising from poorly implemented security protocols by the developers who wrote the code. This is caused by an emphasis on usability and openness and the assumption that JavaScript is secure.
The chances are good that you’re not at risk. But if security is a top priority, it might be a good idea to turn JavaScript off.
How to Turn JavaScript Back Off
Take the same steps as before: go to Chrome > Settings > Advanced > Site Settings > JavaScript, and toggle the switch over to Blocked.
Should you enable JavaScript or not?
For most users, JavaScript is pretty safe. If you’re doing something that makes you particularly concerned about security, you can turn JavaScript off, then easily turn it back on. But to get the most out of the modern web, it’s best to leave it on.
Another option is to turn off JavaScript on specific websites. It’ll still be enabled by default but won’t be used every time you go to that website. This is great for content or news sites that throw a ton of adds at you. Turning JavaScript off makes the site a lot easier to read.

