The Beginner’s Guide to Azure Security
Microsoft Azure is an integrated set of cloud services that allow companies to develop and deploy web applications at scale.
Approximately 95% of Fortune 500 companies use Azure because of its power, reliability, and flexibility. Built on top of Microsoft’s world-class infrastructure and software, Azure supports virtually every language, many open-source technologies, and meets more compliance standards than any of its peers.
Azure security is phenomenal, which is perhaps the biggest reason why enterprise clients feel safe in moving sensitive data to the Microsoft cloud. The company continues to invest billions in designing, monitoring, and evolving their infrastructure to meet the latest threats.
At the end of the day, however, Azure security is a team effort. While Microsoft provides best-in-class infrastructure, customers are responsible for protecting what they build.
Let’s go through the main aspects of Azure security, as well as the tools Microsoft provides for users to fortify workloads and data in the cloud.
What makes Azure secure?
The global infrastructure that supports Azure is extremely reliable, protected by state of the art technology, and overseen by some of the world’s leading computer science minds.
There are over 60 geographically dispersed regions of service, supported by more than 100 Microsoft datacenters. Datacenters are highly secure and their infrastructure comply with a comprehensive set of international and industry-specific standards, including:
- FedRAMP
- HIPAA
- ISO 27001
- SOC 1
- SOC 2
The network connecting these datacenters is extremely resilient. It includes content distribution, load balancing, redundancy, as well as data-link layer encryption to protect all Azure traffic. This prevents snooping, wiretapping, and man-in-the-middle attacks. And, because this technology is integrated in the network hardware, the added encryption does not increase latency.
More than 3,500 security professionals are employed by Microsoft to keep their cloud secure 24/7/365. They analyze security telemetry on a massive scale, harvest information about the latest threats from network points across the globe, and deliver continually updating solutions to their customers.
For Microsoft 365 services alone, the company handles an extraordinary number of incidents each month:
- 5 billion threats blocked across network points
- 400 billion email analyzed through spam/phishing filters
- 450 billion authentications against Azure Active Directory
Leveraging Microsoft Graph, AI, and advanced machine learning, Microsoft’s Cyber Defense Operations Center and Microsoft Security Response Center are able monitor trillions of daily signals across their global ecosystem. They detect and develop actionable responses to keep maintain the integrity of their network
Anytime one Azure customer faces a new botnet attack, malicious actor, or malware executable, all other customers are made aware, and the vulnerability is remediated immediately.
Shared Responsibility for Azure Security
Microsoft also uses their trove of threat intelligence information to develop and refine the full suite of in-house cybersecurity, governance, and compliance tools that protect Azure.
As powerful as these tools are, however, it is up to the customer to understand what they do, how to enable them, manage them, and track their performance.
Microsoft respects the privacy of your data, and allows you to configure your infrastructure to fit your needs. The tradeoff is that they cannot be fully responsible for protecting your cloud environment. As this visualization of Microsoft’s shared responsibility model explains:
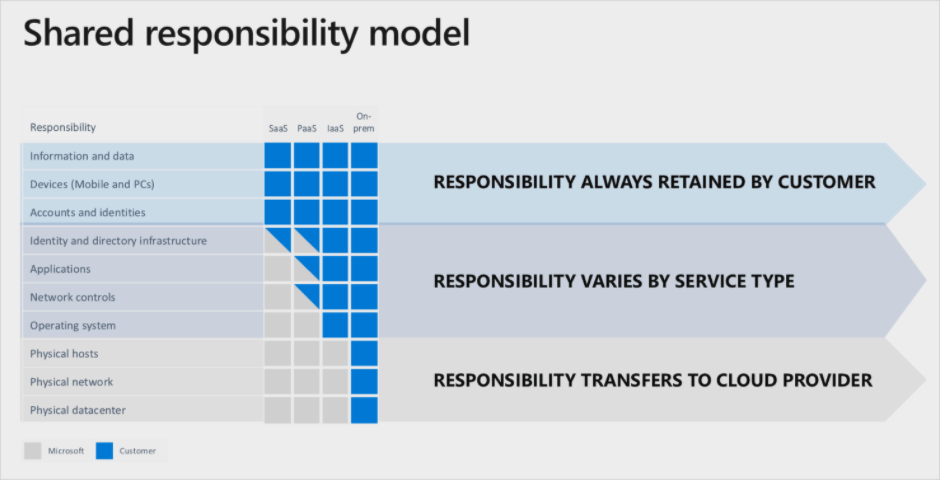
The boundary between Microsoft/customer responsibility depends on the Azure service in question. Practically speaking, the greater control you have over a particular service, the greater your responsibilities.
That said, Microsoft has done everything in their power to give you the tools you need to shore up your Azure security.
Azure Security Features and Services
For each Azure service, there are purpose-built features and options that streamline the task of hardening your entire environment. Everything has native integration, which simplifies management across all users and devices.
Here are the most common and critical Azure security features, broken down into four key areas:
- Data Protection
- Identity and Access Management
- Network Security
- Threat Detection and Response
Data Protection
To promote efficiency and keep costs low, multiple customer deployments are stored on the same physical hardware in Azure (this is no different from AWS or Google Cloud). Azure enforces logical isolation to keep data segregated, preventing one customer from accessing another’s cloud assets.
There are many ways to backup and encrypt data to make sure it is always available and protected. Using Azure Key Vault, you can safeguard the encryption keys provided by Azure, or manage your own keys.
Data redundancy: You have multiple options for how you want to replicate your data, and where it is stored. There are three options available:
- Locally redundant storage maintains three copies of your data, which are replicated three times within a single facility.
- Zone-redundant storage maintains three copies of your data, which is replicated three times across two to three facilities, and may be spread across two regions.
- Geo-redundant storage maintains six copies of your data, which is replicated three times in your primary region and three times in a secondary region.
Data at rest protections: By default, data is encrypted when it’s written into Azure storage, and decrypted when accessed. Additional default encryptions are in place for services like Azure Cosmos DB and Azure Data Lake.
All at-rest cloud resources can be protected by tools or enabling Azure security features like:
- Azure Disk Encryption for VMs and disks
- Transparent Data Encryption and Always Encrypted for databases
Data in transit protections: In addition to the default data-link layer encryption, Azure has a number of features customers can use to move within their cloud and outside the organization, including:
- Ability to use transport layer security (TLS) protocol with perfect forward secrecy to authenticate and ensure the privacy of data in transit between customers and your cloud services.
- Server Message Block (SMB) encryption for data in transit over Azure virtual networks
- Remote Desktop Protocol (RDP) sessions are protected by TLS
- Secure Shell (SSH) to connect Linux VMs
- Azure VPN Gateway for traffic over hybrid deployments with IPsec for transport encryption
- Secure Socket Tunneling Protocol (SSTP) to create VPN tunnels
Identity and Access Management
Azure Active Directory (Azure AD) allows you to register devices and manage access controls across all of your on-premise and cloud services. You can ensure that your resources are always available to employees and customers with valid needs, and completely inaccessible to everyone else.
Azure AD offers real-time visibility into identity-based threats, such as suspicious sign-in activity, with the ability to drill down into user-specific reports. Some of the key security capabilities and services include:
- Azure AD access reviews to manage roles, permissions and access at scale.
- Azure role-based access control (Azure RBAC) provides comprehensive authorization management with built-in and custom roles.
- Azure AD B2C for consumer-facing applications to manage millions of identities.
- Azure AD Connect, which creates a common user identity across hybrid deployments.
- Azure AD Identity Protection, which helps organizations detect and investigate identity-based threats.
- Multi-Factor Authentication adds an extra layer of security, requiring strong, simple authentication via a range of verification options.
- Azure AD Privileged Identity Management, which lets you monitor and control access of users with administrator privileges
- Single sign-on allows individuals to sign in once for access to all of the apps and resources
Network Security
Azure provides a robust set of tools that help you make sure that all of the traffic across your network is legitimate and there are no access points open for any would-be attacker.
At the network layer, administrators can control access using Azure network security groups (NSGs), which is a basic, stateful, packet filtering firewall. NSGs allow you to filter network traffic between resources in Azure default security rules, or customizable augmented security rules.
To streamline the configuration of NSGs and minimize mistakes, you can use service tags and application security groups.
One of the best network security features on Azure is just-in-time (JIT) access, which helps you lock down the inbound traffic to your VMs. With JIT access, users make requests, get authorization from Azure RBAC, and are granted a pre-set amount of time to access the VM. Once the time has expired, inbound traffic is denied again.
Threat Detection and Response
Signals from across all of your Azure subscriptions are aggregated, analyzed, and displayed on the Azure Security Center. You get an overhead view of the entire company’s security posture, with threats and compliance issues automatically flagged and prioritized according to severity.
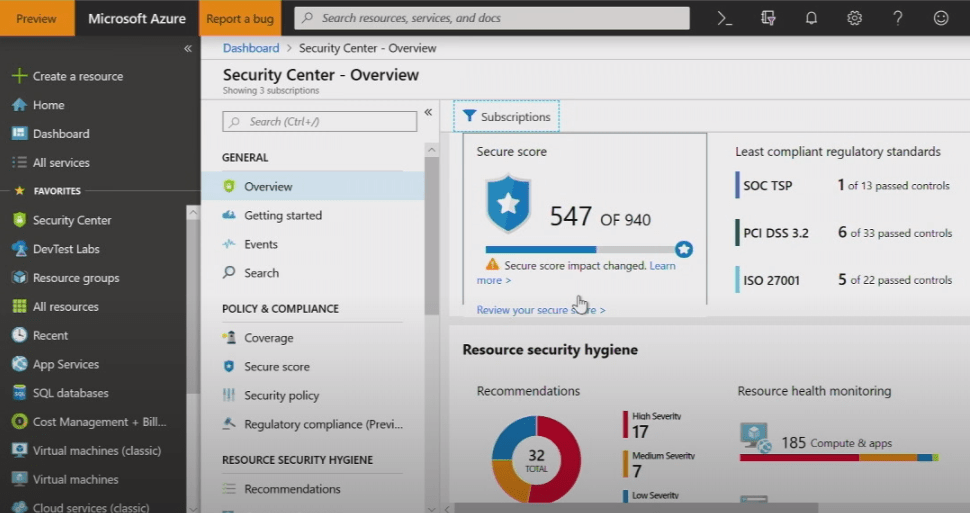
Azure Security Center continuously discovers new resources as they are deployed, and makes recommendations based on best practices.
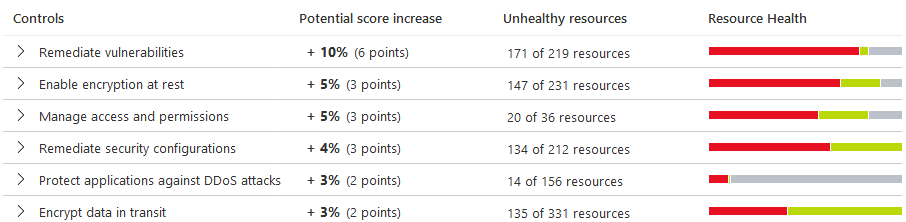
On the main dashboard, there is a security score based on a number of risk factors. You can see exactly where this score comes from, and how to improve it based on reconfiguring resources, enabling IAM controls, controlling policies, and so on.
Each issue can be investigated down to the user or file level and remediated directly. Where problems cannot be solved with a few clicks, links to documentation are provided.
Azure Security Center integrates with Microsoft Defender Advanced Threat Protection (ATP), which constantly scans for suspicious activity. In effect, Azure Security Center becomes a centralized hub for endpoint detection and response across all of your services.
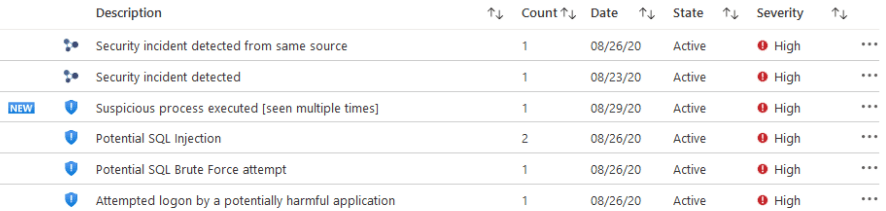
These automated recommendations are based on advanced analytics linked to Intelligence Security Graph, as well as data generated by Microsoft security teams and threat hunters.
What this means is that you get a complete view of every threat. Microsoft leverages their deep experience and massive scale to make sure that every type of known threat is accounted for. Fileless attacks, hidden malware, malicious PowerShell scripts, and other recent threats will trigger alerts.
What you should expect to do yourself to keep Azure secure
Regardless of the Azure services you choose, there are several aspects of Azure security that you will always be responsible for:
- Data and information you store on Azure
- Endpoints you connect to Azure
- Accounts and identities you give access to
With the IaaS services, there are additional responsibilities, including the OS, infrastructure configuration, and network controls.
Be aware of how each service you use increases your attack surface, and the tools provided by Microsoft to address these new potential gaps in security. Operationalizing the best practices and patterns for Azure security is critical for maintaining the integrity of your cloud environment.
How is Azure different from other cloud service platforms?
Azure is 100% a Microsoft product. It is sturdy once you get it up and running, and nearly impossible to beat once IT administrators gain fluency.
With so many tools to control policies, access, network configurations, and so on, the upside is granular control over your entire Azure ecosystem. This is also the downside, however, if you haven’t provided enough training and support to those in charge of Azure security.
With great power comes great responsibility.
No IaaS service is “easy” to use, out of the box, but Google Cloud is a little more inviting to new users. The tradeoff is that Azure offers more services with greater customizability, though Google Cloud is rapidly closing ground.
Amazon Web Services (AWS) has an even richer set of cloud service solutions and deeper developer functionality than Azure. It has sustained its first-mover advantages, even with Azure and Google Cloud making significant investments, because AWS continues to roll out new features and invest in the security of their infrastructure.
Where Azure steps away from both Google Cloud and AWS is its integration with other Microsoft products. Companies can use Microsoft 365 and Azure for virtually all business operations, limiting the number of vendors and decreasing their attack surface.
The native integration of the Microsoft infrastructure speeds deployment and simplifies configuration, management, and automation. For companies with hybrid deployments, the Azure stack continues to be the number one choice.
All three of the major vendors have excellent products with top-notch security. If you have already invested heavily in a Microsoft environment, moving cloud operations to Azure is the obvious choice.
Shop around, but you should have a compelling reason to divide services between vendors, and give up the unified security suite provided by Microsoft.

